Reinforcing Cybersecurity: The Imperative of Posture Checking for Remote Workers
In today’s ever-changing digital business landscape, where remote and hybrid work models are rapidly becoming the standard, the safety of a company’s data and network infrastructure is an ongoing and pressing problem. If you are your company’s Chief Information Security Officer (CISO) or the CIO, safeguarding your remote workforce is your top priority. “Posture checking”, an essential element of any security strategy, evaluates the current security standing of a remote computing device before allowing the device to connect to a network.
The Posture Check Imperative
Before accessing confidential company information, remote workers’ devices should be subjected to posture checking, which serves as the first line of defense and ensures that all necessary security standards have been met. This involves verifying that the antivirus software is up to date, that the firewalls are enabled, and that the operating system has been updated. If these tests are skipped, there is a higher likelihood that your company could fall victim to data breaches, virus attacks, and other forms of cybercrime.
Imagine a scenario in which a distant worker accesses critical company data via a personal device that hasn’t been updated in several months. This device is vulnerable and offers an easy target for cybercriminals who could go on to access the entire network and compromise sensitive information. In this situation, had a posture check been conducted, access would have been prevented until the device satisfied the security criteria established by the IT team. Thanks to posture checking, the risk to the organization of a security breach is significantly reduced.
Furthermore, the use of posture checking helps to instill a sense of security awareness in the workforce. When staff are made aware that their devices are subjected to routine audits to ensure they comply with security standards, they are more likely to keep their equipment up to date, improving the organization’s overall security posture.
The Workspot Cloud PC platform stands out among the many available end-user computing solutions for its zero-trust security capabilities, including robust posture-checking methods. Implementing such a solution can significantly improve your organization’s cybersecurity posture.
This tech note explores Workspot’s posture check capabilities and how this important feature works for customers. Contact your Workspot Customer Success champion or login to the Workspot Community portal for a step-by-step configuration guide.
The Workspot Posture Check Feature
Let’s examine the capabilities necessary for any organization to build a solid security framework and how Workspot posture-checking capabilities support this framework. This section reveals the essential compliance criteria the Workspot Client for Windows can assess, offering an additional layer of protection for Windows 10 and 11.
Before permitting an end-user to connect to remote Workspot desktops and applications, the Workspot Client for Windows can perform an optional security posture check. This helps to confirm that the client is operating on a device that fulfills the security requirements established by your organization. This posture check is set up in Workspot Control as a comprehensive security policy element.
The Workspot Client for Windows can check for the following conditions:
- Windows version: Is the device running the minimum release number specified for Windows 10 and 11?
- Windows Update: How outdated is the device operating system compared to the latest Microsoft Update patch?
- Antivirus Enabled: Is an antivirus package currently running?
- Firewall Enabled: Is a firewall currently enabled?
- Connected via Wi-Fi: Is a Wi-Fi connection allowed? Or must it be a wired-only network connection?
- Running in a VM: Does your organization allow end-users to run Windows on a virtual machine? (The Workspot Client is not supported on virtual machines.)
- Connection Origin (Geolocation): Coming soon! Is the Workspot Client trying to connect from a disallowed country?
- Domain Joined: Is Windows joined to a mandatory AD domain?
- Processes/Services: Are other specified processes and services running?
- Custom Script: Has a custom script (optional) reported success?
Understanding these capabilities is crucial for any business seeking to strengthen its cybersecurity posture, especially in an era where remote work is prevalent. From the Windows version to specific running processes, these checks form a comprehensive security protocol to shield your organization from cyber threats. Let’s take a closer look at how this feature set works:
How it Works
A posture check is carried out as the initial phase of the sign-in procedure whenever an end-user logs into Workspot Client for Windows and launches a desktop or application. This is displayed in the popup that shows the connection’s progress:
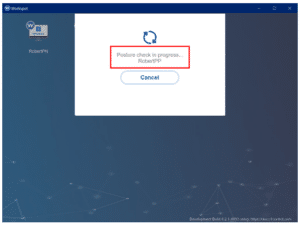
Workspot Client will connect the user to the distant resource if the posture check is successful. If it fails, a warning or a failure popup will appear. This is determined by whether or not the security policy specified in Workspot Control is designed by your IT team to either warn the user about which requirements have not been met or to prohibit access.
Configuring Posture Check in Workspot
Workspot Control is used to put the posture check capabilities to work to help protect your organization. Knowing what kinds of checks to run and how to set them up most efficiently is essential to sustaining a strong cybersecurity posture over time.
Workspot Control’s default setting does not enable posture checking so as the watchful protector of your organization’s cybersecurity, you are responsible for implementing it. A detailed guide for easily configuring posture checking is available from your Customer Success champion at Workspot or from the Workspot Community site.
Microsoft Windows Version: You can set a minimum version number (build number) for Microsoft Windows 10 and 11. Checks for the two operating systems are configured independently.
Microsoft Windows Update: The Windows Update option lets you warn or deny users running a Windows version released several days ago.
Antivirus and Firewall: The Workspot Client checks with Windows to see if antivirus and firewall protection are active.
Client Environment (Miscellaneous Checks): Additional, more specialized tests are also available:
- Connected via Wi-Fi. Use this if you wish to discourage or forbid users from connecting over anything but wired network connections.
- Running in a VM. You can enforce this here if you don’t allow users to connect from a virtual machine. The Client can detect the most popular VM types.
- Geolocation (connection origin): Coming soon! Checks the apparent location of the Client. Use this to allow connections only if they appear to originate in certain countries or to forbid a list of countries. This feature uses three-letter ISO codes such as “USA”—separate multiple entries with commas.
- Domain joined: Use this if you only recommend/allow end-users to connect via Windows computers connected to an approved AD domain. This can help prevent random computers from connecting to your Workspot desktops.
Process/Service Checks: With Workspot Client for Windows 5.0 or higher, you can also check to see if specified processes and services are running and set actions for when they are running.
Custom Script: With Workspot Client for Windows 5.0 or higher, you can specify a custom PowerShell script for the Client to download and run, with success/failure determined by its exit status. The Workspot Client will run these tests along with other posture-check tests you specify.
Conclusion
As businesses continue to adapt to remote work, integrating posture checking into your security strategy is no longer optional; it is a necessity. Posture checking fortifies your defenses against cyber threats and fosters a security-conscious culture among your workforce. As an IT or business executive, embracing such proactive measures is integral to ensure that the transition to remote work doesn’t compromise the security of your business.