Secure Access to Virtual Desktops & Apps
Workspot Client enables secure access to:
- Windows 10 /11 Desktops: Access to virtual desktops hosted in Microsoft Azure, Google Cloud Platform, AWS and on-premises datacenters.
- Windows Applications: Workspot Client is integrated with industry leading H.264 based RDP10.x protocol stack and enables access to an application running on Windows Server 2012 and above. Deep integration with Microsoft RDSH Service enables seamless delivery to Windows applications.
- Web Applications: There is a secure browser bundled into Workspot that enables access to web applications such as SAP, SharePoint, etc.

Workspot Client presents all of the icons that represent the virtual resources available to each user.
Securing Data in Motion
All communication to Workspot Control and cloud assets are protected with SSL/TLS. The embedded network stack enables secure L4-L7 access to network resources. The client implements a split tunnel that allows Workspot Client to be connected simultaneously to both the corporate and public networks. Application traffic can be routed to either network based on IT policies. Workspot is using a FIPS compliant TLS/SSL library in the embedded network stack.
Securing Data at Rest
All configuration information inside Workspot Client is encrypted with a multi-layer scheme using industry standard AES-256 encryption.
- All assets are encrypted in memory before they touch the file system. Every object is encrypted using a different key.
- Each key is encrypted using a master key.
- The master key is encrypted with a user specified PIN that is not stored on the device. The user can access the Workspot application only when they can successfully provide the PIN or authenticate with Microsoft Azure AD or Microsoft AD credentials.
Secure Access Using Azure AD
Workspot Client is a downloadable application for the end user’s device, whether corporate – or personally-owned. It ensures secure access by conducting device posture checks, securing data in motion and at rest, whitelisting and blacklisting traffic, and logging events for compliance and auditing.
When a user logs in, based on the configuration IT specifies, the user can be challenged to authenticate against Microsoft Azure AD or an AD Domain Controller in the cloud or on-prem. All existing Workspot security policies configured to work with your AD Groups are embraced and used to unlock Workspot Client. Conditional access policies are supported transparently in Workspot Client because of deep integration with your AD configuration.
Upon initial login, users provide their Active Directory (AD) credentials for authentication. Workspot Client can be configured to encrypt and cache credentials to be used automatically on subsequent logins.
Secure Access with PIN
When a user launches Workspot Client for the first time on their device, the user is prompted for their AD credentials for authentication (which are then encrypted and stored) and then they are prompted to create a PIN for Workspot Client on that device. The next time the user launches Workspot Client, the AD credentials are provided via SSO (single sign on) and only the PIN is required. The PIN is validated against the client master secret (CMS). If the CMS can be decrypted, the PIN is deemed valid; otherwise the PIN is invalid.
Incorrect PIN entries are subject to increasing wait times to circumvent brute force attacks. Workspot Client will allow up to 5 invalid PIN entries after which the data inside Workspot Client will be wiped from the device, thereby keeping the organization’s assets secure.
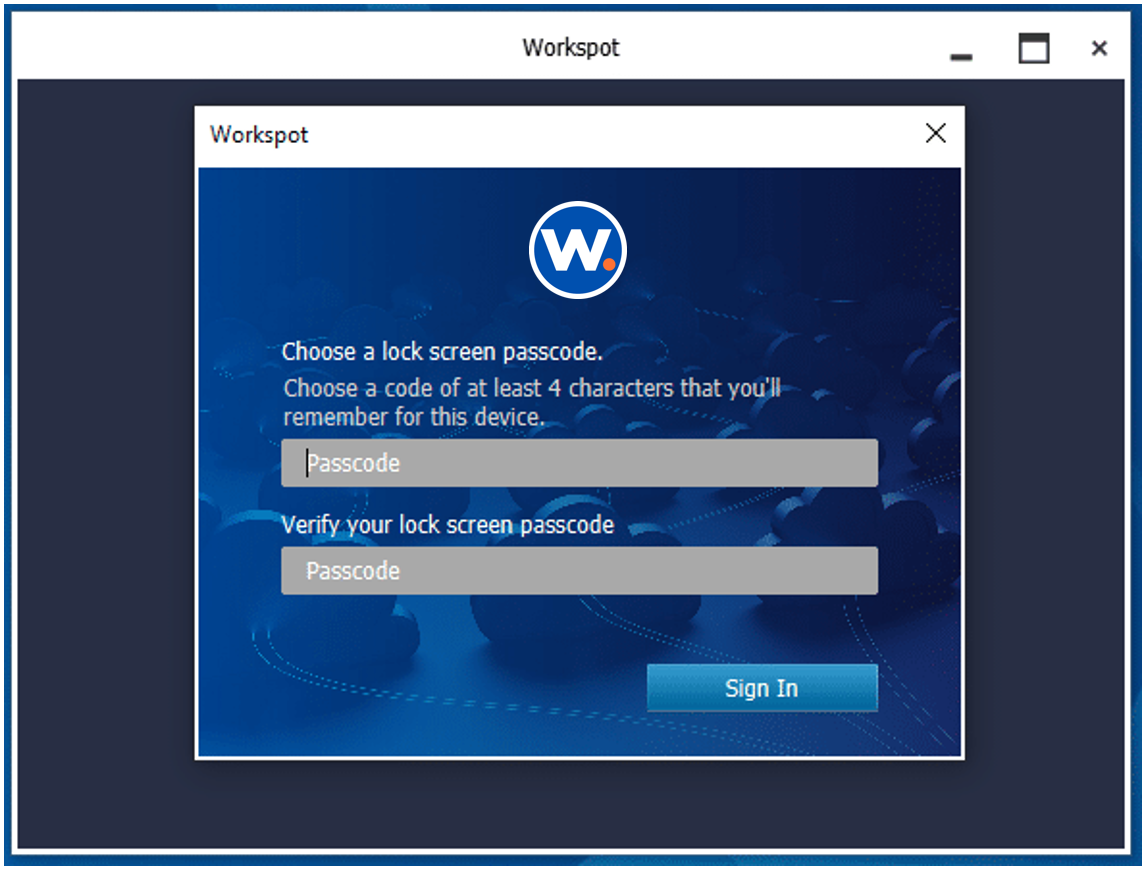
Once authenticated to AD, users can set a PIN, which is all that’s required on subsequent logins to provide single-sign-on
Whitelist / Blacklist Traffic
IT can control which sites the user can and cannot visit from inside Workspot Client by configuring a blacklist/whitelist. Browser based apps can leverage this feature for restricted intranet access.
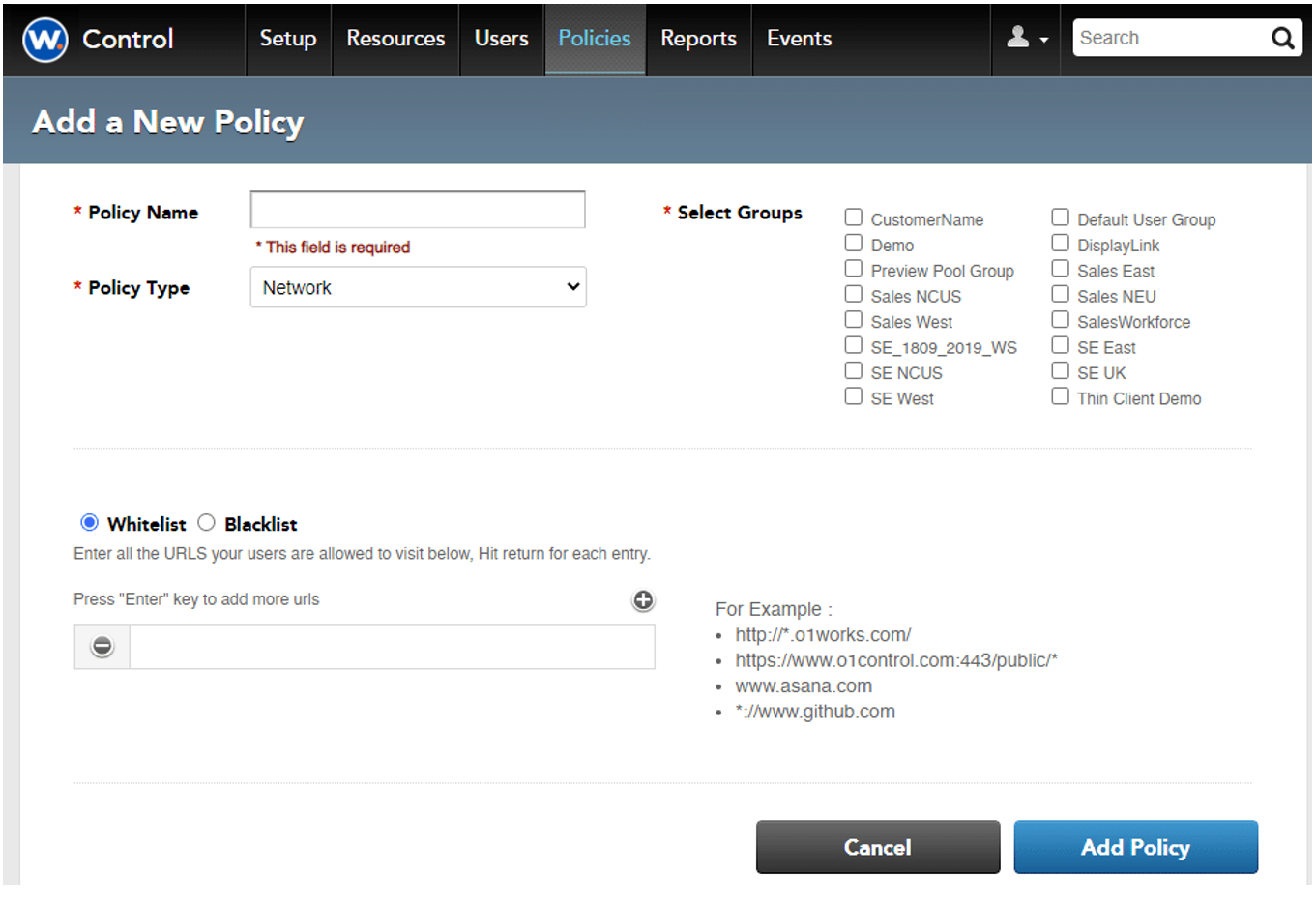
Specify which URLs can be allowed access (White List) or specifically denied access (Black List).
Big Data Contextual Security
When a user accesses their organization’s IT assets, Workspot Client collects contextual data about who did what, when, where, and how. Workspot cannot see this data and only collects it for relevant business activity – it does not collect data from personal applications such as Facebook – on the device. This data can be used for regulatory and compliance purposes, auditing, and adaptive authentication.
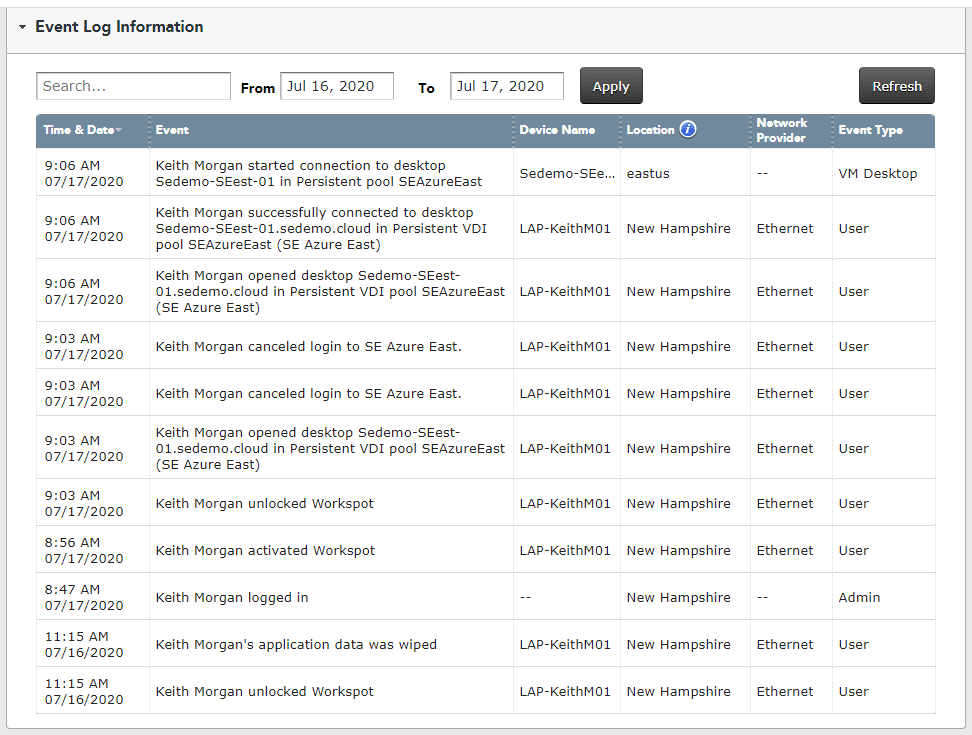
Workspot Client continuously monitors system activity and reports it to Workspot Control for use in identifying usage patterns and anomalies.
Additional Resources
We’re here to help! Access these valuable resources to help guide your journey to modern end user computing.