Global, Single Pane of Glass Management
The Workspot Enterprise VDI platform was architected to ensure a highly efficient and secure environment. IT teams use Workspot Control, a single pane of glass administration console, to provision and manage their global virtual desktop and app deployment across on-premises datacenters and multiple public clouds and cloud regions. Built for massive scalability, it’s easy to add new virtual desktops anywhere in the world in a few minutes, then monitor and analyze activity data globally – all from one admin console.
Control & Data Plane Separation
Workspot’s innovative control/data plane separation is a fundamental architecture decision. This separation is critical from a data security perspective, and delivers many other benefits. The control plane has two major functions:
- Set up, provision and manage all virtual desktops and apps
- Establish secure communication with end user devices for pushing corporate policies
Once the session is established (and the user has been authenticated), the user accesses the virtual resources directly from the cloud. Throughout the connection process, no user credentials are stored in Workspot Control. Workspot Control only authorizes the user, but authentication is delegated to Active Directory or Azure Active Directory using a Workspot Connector installed on-premises in the customer’s data center.
When the user is using Workspot to access business apps and data on their device, all the data flows back and forth directly between the client and business applications via the data plane. No application data flows through Workspot Control. Additionally, no business applications or data traverse Workspot Control. This unique security advantage is possible because of Workspot’s innovative architecture, and it’s how we extend your Zero Trust Security posture.
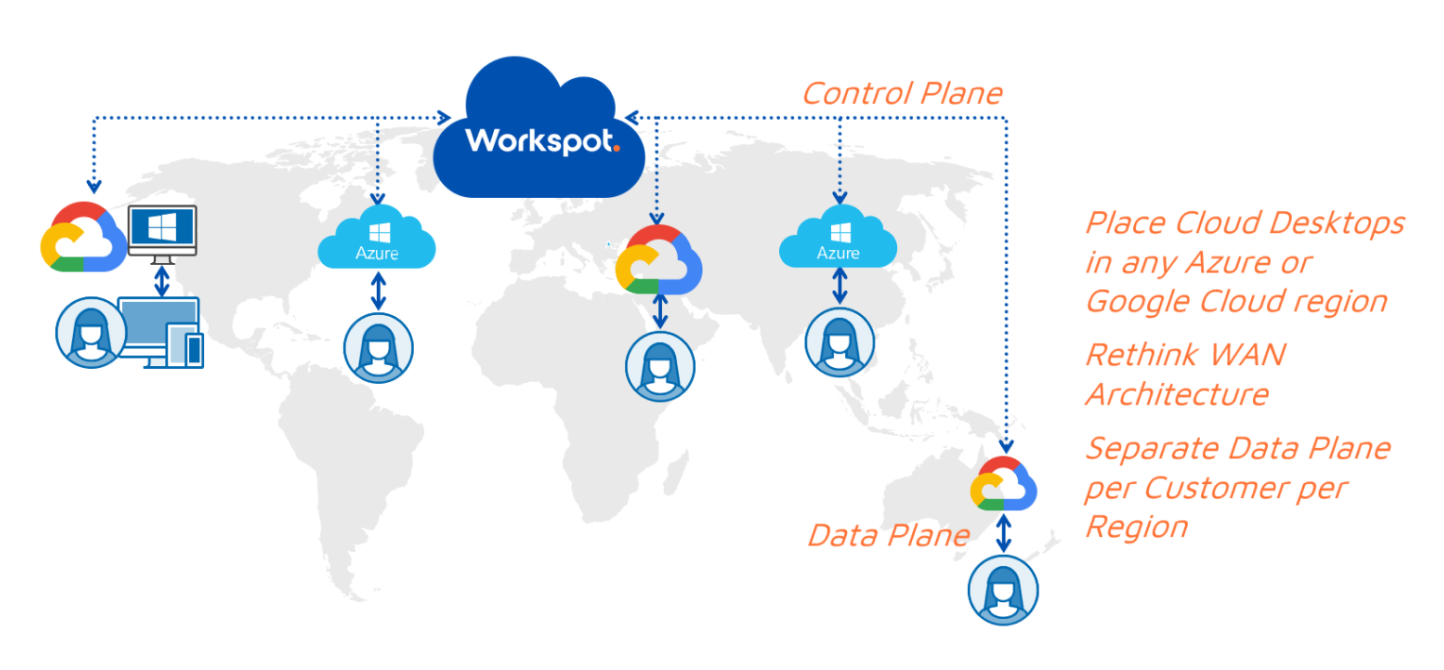
Separating the Control Plane and Data Plane allows Workspot to support virtually unlimited numbers of users, with performance they love, while improving your security posture.
Security Policies Configuration
With Workspot, IT teams are fully in control of their deployment. We make it easy to extend your existing security and authentication policy to your Workspot deployment. IT simply configures Workspot Client behavior using the Workspot Control console. Manageable behaviors ensure that each user has precise access to apps, data and capabilities needed to perform their jobs. Examples include:
- Restricting access to applications based on username or group membership
- Restricting copy and paste based on user trust level in the organization
- Restricting printing functionality for remote users
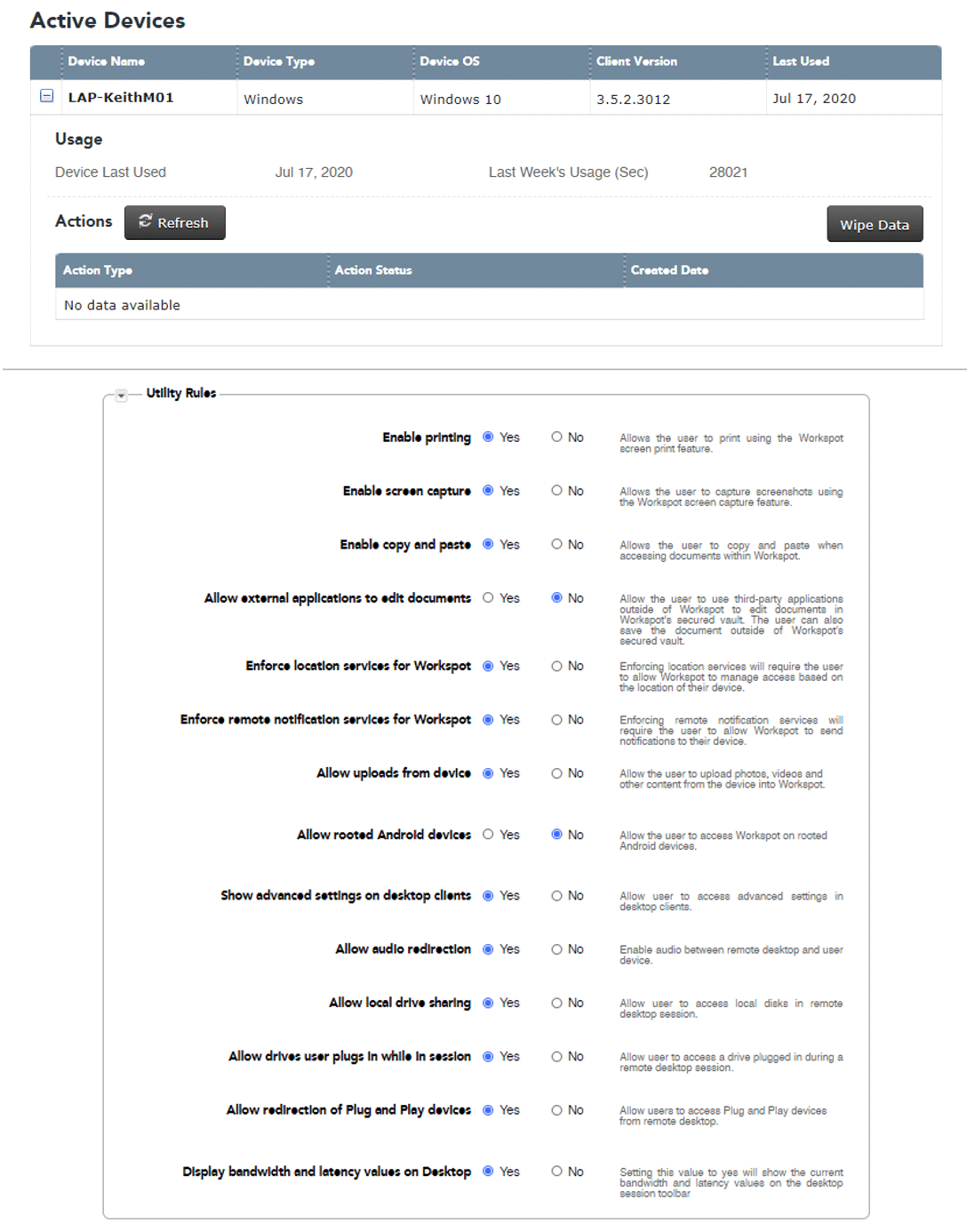
Specify the security policies you require by group or individual, quickly make security adjustments, then enforce them across all the appropriate users and groups.
Remote Wipe Data
Workspot makes it simple and secure to support BYOD. IT must ensure that corporate assets are isolated from a user’s personal apps and content. Workspot Control provides IT the capability to easily remote-wipe any corporate data, including cached configuration and cookies, that resides inside the Workspot Client on the user’s device. Data outside the Workspot Client is unaffected by the remote wipe operation, so a user’s personal apps and data stays intact.
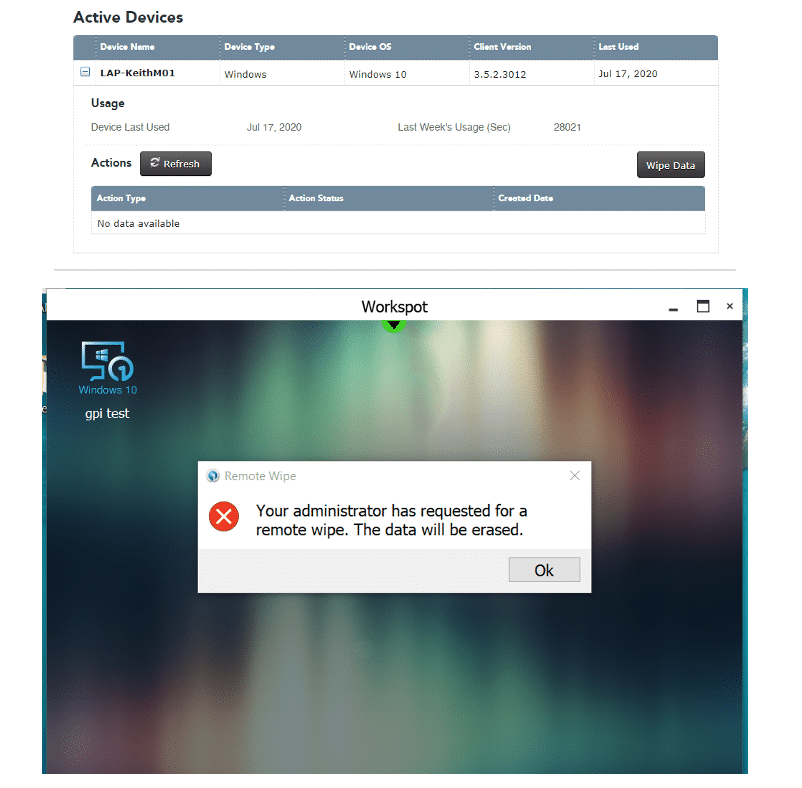
Run the Workspot Client on the user’s BYOD device, and when the work is done, run a Remote Wipe operation to surgically remove Workspot from the user’s personal device.
API Access for ITSM
Workspot provides a set of REST APIs for IT Service Management (ITSM), automation and/or scripting tools, that enable your enterprise to automate the workflow of virtual desktop provisioning. IT can leverage existing ITSM workflows on platforms such as ServiceNow or BMC Remedy, or they can build their own scripted solutions to orchestrate the provisioning and lifecycle of users’ virtual desktops.
Workspot APIs can be used to automate Workspot functionality for adding/deleting users, creating/deleting virtual desktop pools, and assigning/re-assigning users to virtual desktop pools. APIs can also be used to get usage reports on user and resource activities. IT developers can use Workspot APIs with PowerShell, JSON and/or Postman to write automation scripts to integrate with their existing ITSM tools.
The APIs also provide valuable insights for IT to monitor users’ virtual desktops and activities and loop the feedback into their existing ITSM platform to get full, end to end visibility of the workflow for all cloud regions globally.
Workspot leverages industry standard OAuth2.0 protocol for authenticating and authorizing remote automation clients.
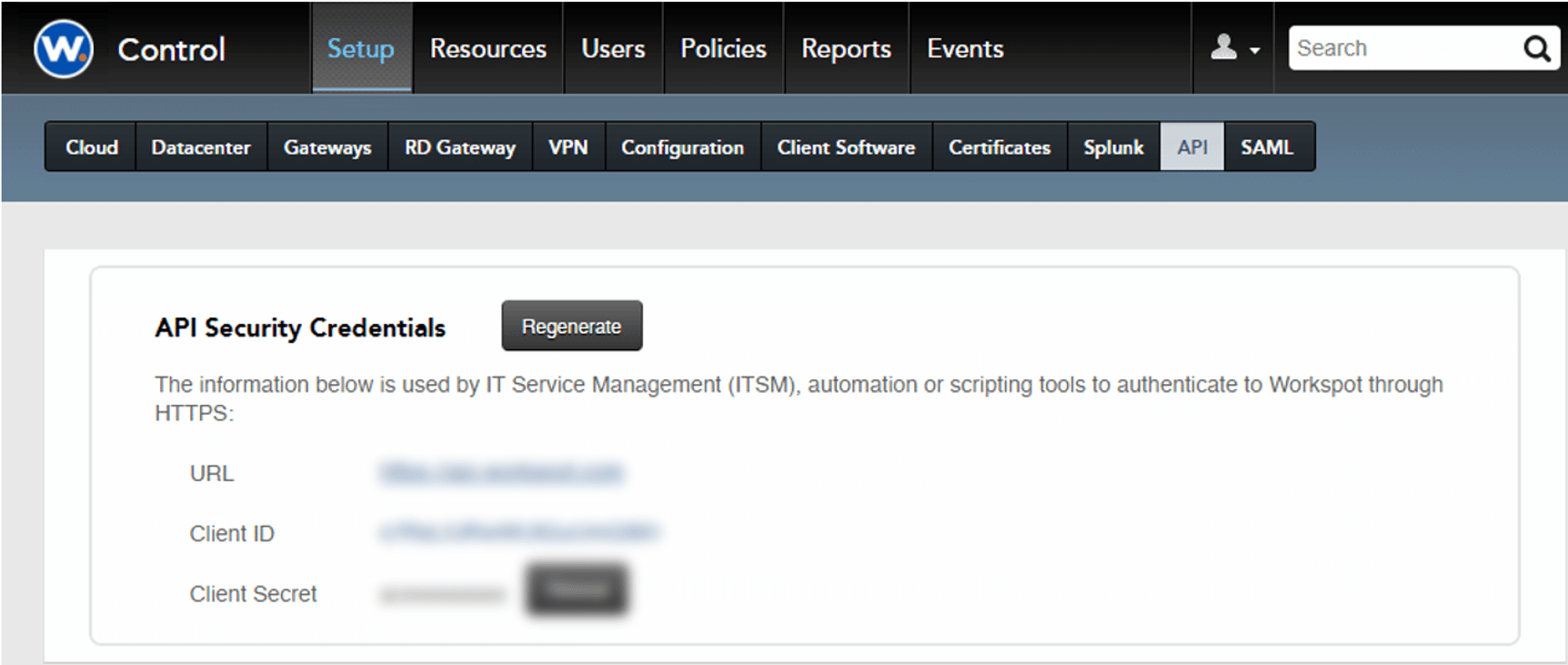
Workspot has a rich set of APIs that automates the virtual desktop lifecycle, user capability management and activity reporting, using PowerShell, JSON and more.
Integration with Splunk
IT can download our Splunk plugin from Workspot Control. The Splunk plugin needs two keys for configuration which are available inside Workspot Control. Once integrated, the Events data from Workspot is delivered into Splunk and can be viewed, searched, and manipulated with standard Splunk tools.
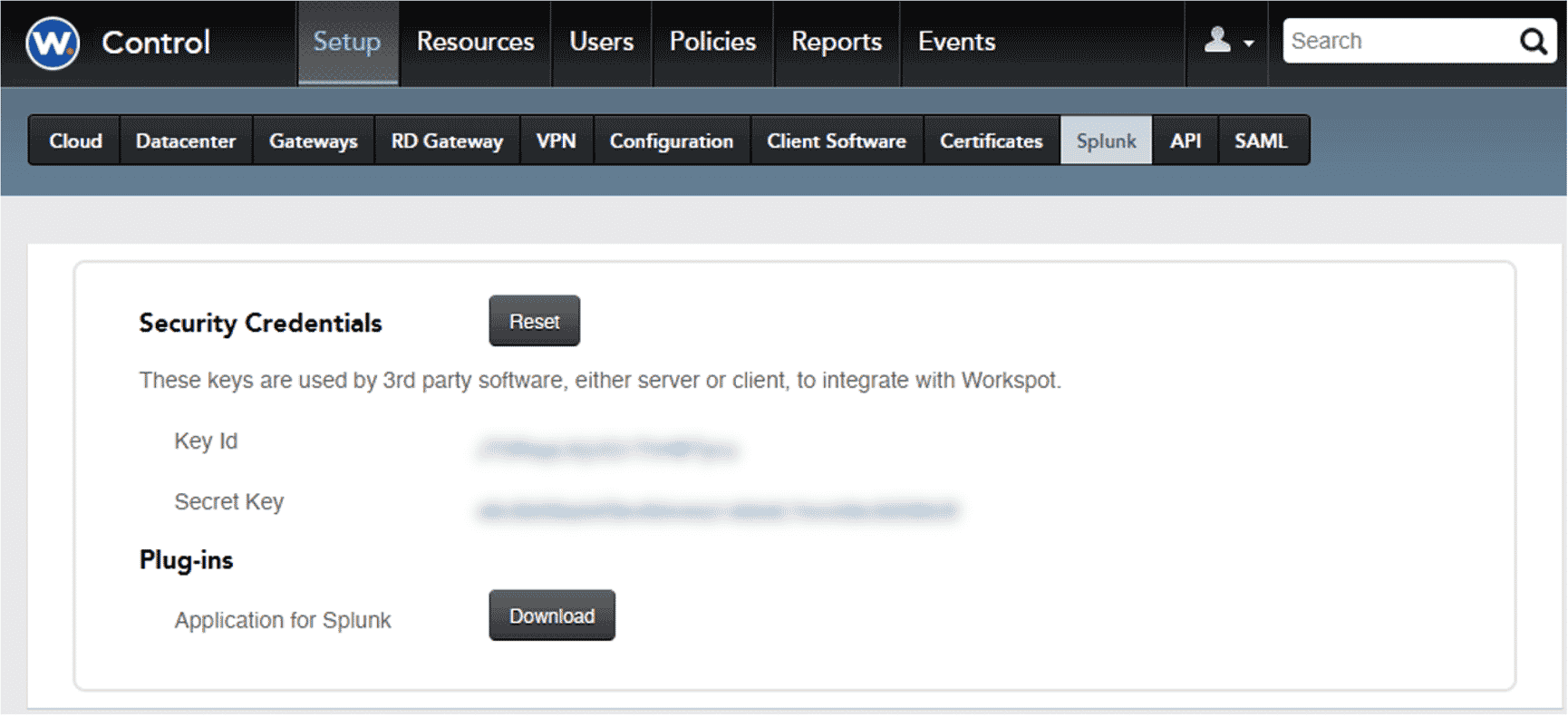
Workspot monitoring gathers event data and can provide it directly to Splunk and other SIEM applications.
Additional Resources
We’re here to help! Access these valuable resources to help guide your journey to modern end user computing.