Guilty Until Proven Innocent
Zero trust security – if your policy is not already in place, it’s time to rethink your approach to information security. Cybercrime – especially ransomware – is the fastest growing crime in the U.S., and the attacks are increasing in number, scope, and sophistication. The Workspot Enterprise VDI Platform was designed to help you enforce your zero trust security policy.
Today, as people use a variety of devices in many different settings, the attack surface is vast, making the case for adopting a Zero Trust Security model. This means that no one is trusted, either inside or outside the organization. To support zero trust, CIOs and CISOs should ask vendors the following questions about virtual desktop security:
- How does your architecture impact information security?
- Where does my data live? Who can see it? How is it protected?
- Where is my Active Directory running?
- What systems are shared between users?
Unlike many virtual desktop solutions, Workspot’s approach to virtual desktop security strengthens your Zero Trust Security model.

Workspot’s multi-layer approach to virtual desktop security is unique in the industry.
Control/Data Plane Separation is Essential for Zero Trust Security
The architecture of the virtual desktop solution really matters when it comes to security. Workspot is the only solution available today that separates the control and data planes. Other VDI solutions are built on outdated architectures that have integrated control and data planes. By definition, when the data and virtual desktop management planes are combined, customer data and authentication systems traverse the same system. Even the VDI vendor could potentially see your data, and that breaks your Zero Trust Security policy.
Workspot’s massive VDI architecture innovation carries with it significant advantages for security, scalability and performance.
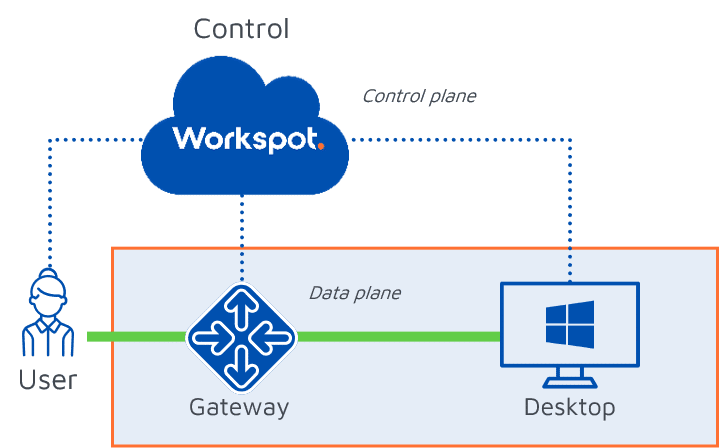
Workspot’s innovative architecture separates the control and data planes, so the user’s tenant is completely isolated.
Multi-factor Authentication
Whenever you need to secure data or intellectual property, you should be using multi-factor authentication (MFA) to ensure zero trust security. Workspot was built for the enterprise, and the platform integrates with your chosen authentication systems. Most of our customers use Azure AD, Azure MFA, Okta, Duo and/or PingID. Workspot supports them all.

Workspot supports your existing MFA solution.
POLP: Principle of Least Privilege
In addition to the architecture decisions we made, Workspot follows the Principle of Least Privilege (POLP), closely tied to the Zero Trust Security policy, for enhanced virtual desktop security. POLP allows for people and processes to only have the bare minimum system access to complete a task. This means that everyone, including the virtual desktop vendors you are considering, needs to prove how they make your organization more secure. With Workspot, you can count on the following:
- An independent security layer prevents unauthorized access to data.
- Users are isolated; if there’s an attack, it’s localized to a single tenant.
- Active Directory is fully under your control, and only you have access.
- You can bring your existing corporate standard AV, AM, DLP and MFA into Azure – no need to create a separate security process.
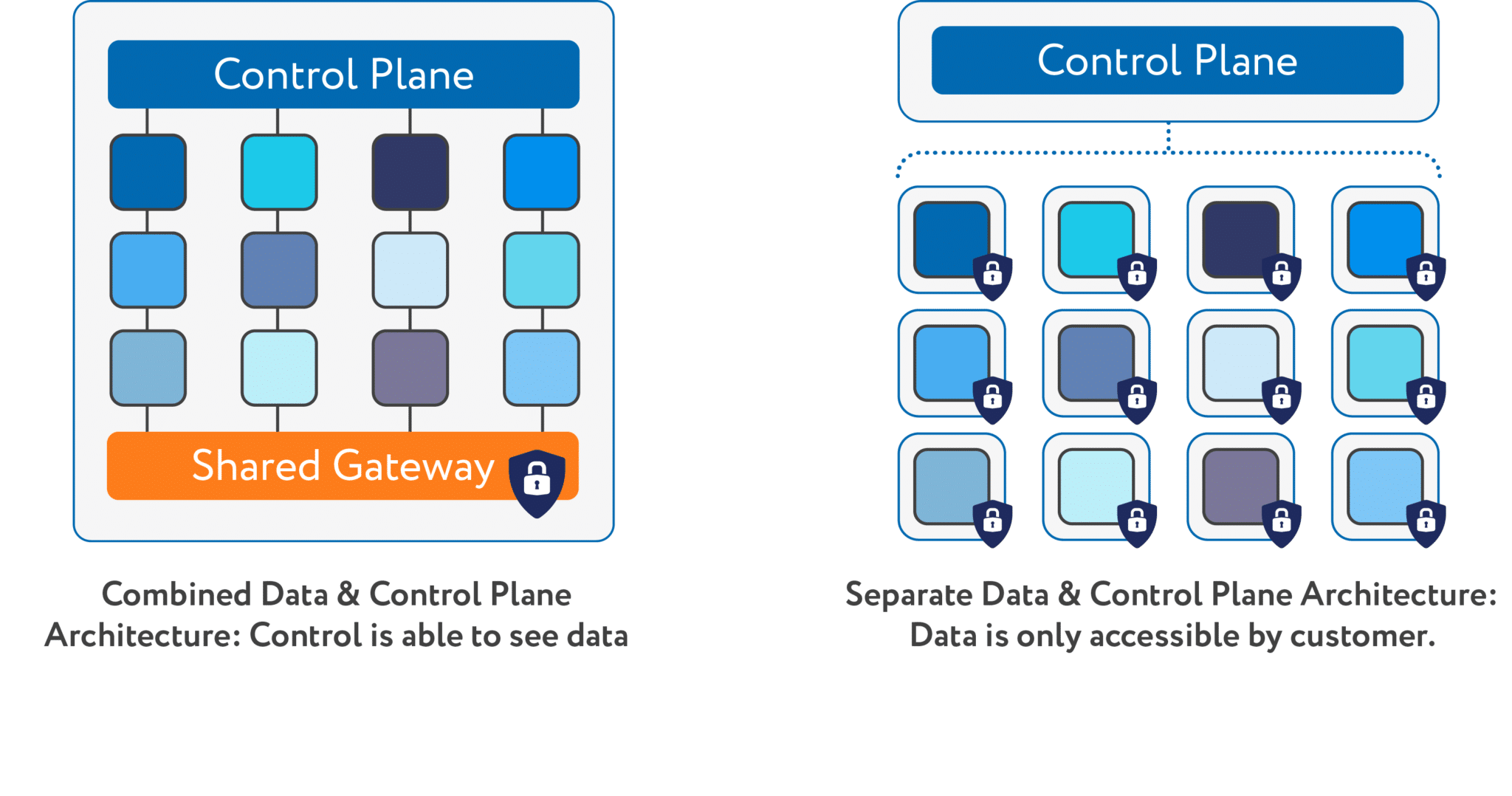
A combined data and management plane (left) jeopardizes your security posture. Workspot separates the management and data planes for zero trust security.
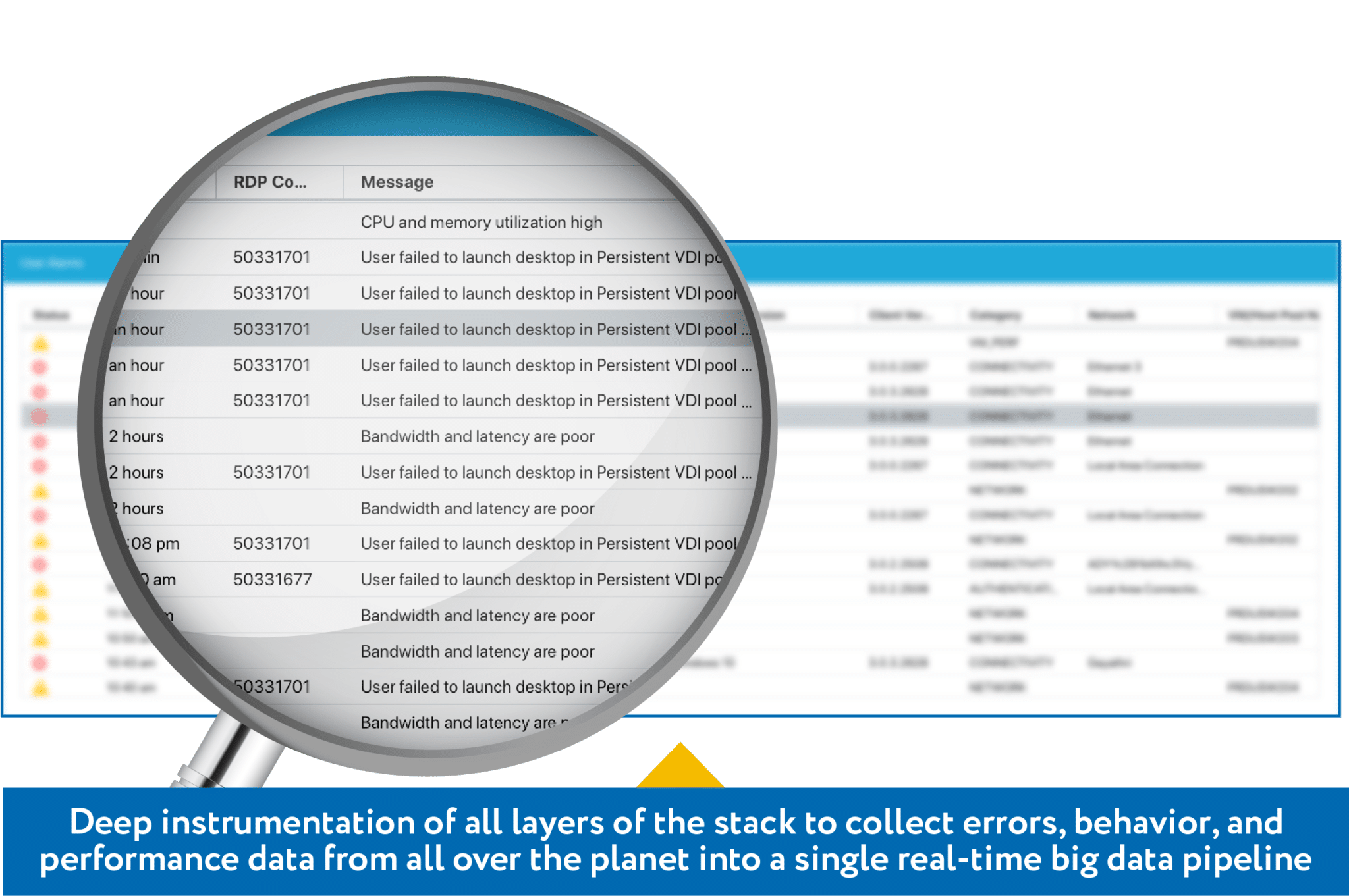
Big Data Visibility
Your IT organization must be able to proactively monitor your global virtual desktop estate. The Workspot Enterprise Desktop Cloud Platform is the only virtual desktop solution that gives you the power to view and manage your entire virtual desktop infrastructure from a single console. Our platform is deeply instrumented, providing a real-time events stream that captures user login attempts and location, as well as the gateways they traverse. APIs also allow you to export this data to other analysis tools such as your existing ITSM and SIEM systems.
Workspot supports your existing MFA solution.
Additional Resources
We’re here to help! Access these valuable resources to help guide your journey to modern end-user computing.