3 Tough Questions CISOs Must Ask Cloud Desktop Vendors
In a recent blog post, we discussed how adopting the right cloud desktop solution can help fulfill an enterprise organization’s Zero Trust security model. Although CIOs and CISOs have reached a greater comfort level with public clouds, the need to conduct broad and deep diligence when evaluating cloud desktop solutions is essential. Each vendor’s approach is architected differently, and architecture matters, especially when it comes to security.
In our discussions with CISOs and other security leaders, the same questions are posed to us again and again, so we have a good understanding of what CISOs care most about. Based on that understanding, we’ve crafted 3 tough cloud desktop security questions you must ask vendors as you evaluate the options for moving desktops workloads to the cloud, – a move that is almost inevitable for enterprises because of the agility and flexibility it brings to enable growth. As attractive as that is, you have to make sure technology choices don’t expose your organization to increased risk. Rather than increase risk, a cloud desktop solution should augment your Zero Trust model. To achieve this, here’s what you need to find out.
Top 3 Cloud Desktop Security Questions for CISOs
Here are the top questions that every CISO should ask a cloud desktop vendor to understand the impact of a vendor’s architecture on your security posture:
1. Where is my Active Directory (AD) running?
What you need to know is – where is authentication happening? And what does it mean to your security posture?
What if the vendor you’re evaluating told you that you must copy your AD to the cloud to work with their service?
Most CISOs tell us that moving AD to the cloud is not desirable for security and complexity reasons. No one wants to touch AD if it is working. No one wants to add more complexity to AD by adding yet another domain controller in the cloud.
What if the vendor told you that their cloud service requires AD authentication to flow through their cloud service? What if that vendor also told you that your AD is running in their cloud service?
Some “cloud” services are based on Windows servers installed in the cloud. They require their Windows components, which are not under your control, to have access to your AD to complete authentication. To keep it simple, they may ask you to install a domain controller in their cloud to make it operationally easy to support their cloud service with your authentication. This means that your authentication credentials are outside of your control and passing through a cloud system that doesn’t belong to you.
If this is ok with you, proceed to the next question. If it’s not ok, it’s time to contact Workspot.
2. What systems are shared between customers?
This is a common question from CISOs for whom enterprise data and intellectual property (IP) protection is top of mind. If protecting IP is a top priority, you need to know whether a vendor’s architecture could expose your IP to outsiders. So to protect all of your enterprise data, you need to ensure that the cloud desktop solution won’t introduce compliance, security, governance and reputation risks. Architecture matters in security, so it’s critical to know that not all cloud desktop systems are architected the same.
If you are the CISO for Brand A, would it be ok for your IP to be stored in the same cloud tenant as your fiercest competitor, Brand B? Not too worried? Well, what if a Brand B employee clicked on an attachment that introduced a virus into brand B’s environment? Could your data be at risk too?
Generally, cloud desktop platforms are based on two architectural models:(1) combined data and management plane or (2) separate data and management planes. Here’s what that looks like:
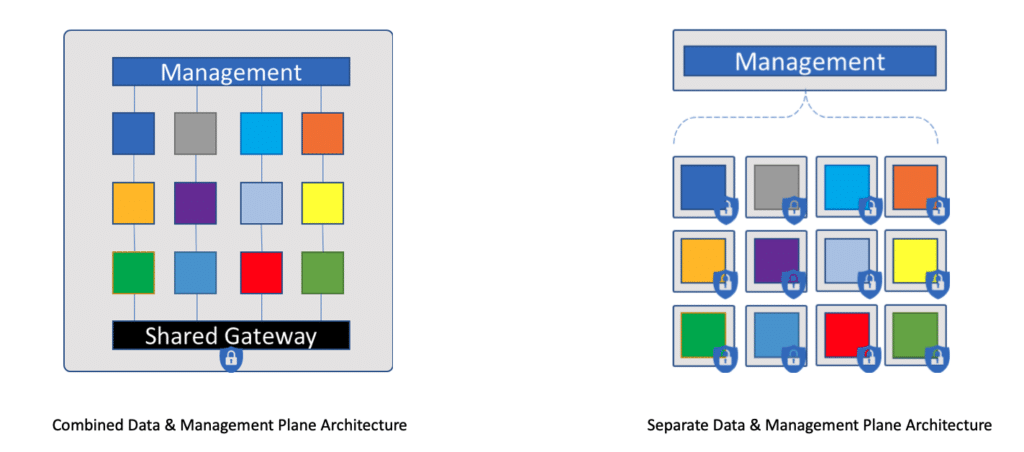
By definition, when the data and cloud desktop management planes are combined, then customer data and authentication systems traverse the same system. The vendor will likely describe the policies that prevent accidental data leakage or unauthorized access. So, a trust model must be established with the vendor, including auditing the vendor for compliance.
In the second model, the management is shared, but the data layer, including the gateway, is completely isolated between customers. Data security risk is greatly reduced with this model. Workspot’s architecture separates the data and management planes
We describe the importance of separating the data and management planes in another blog here.
3. Where does my data live? Who can see it? How is it protected?
The most common answers are TLS 1.2 in flight and AES 256-bit at rest. However, those are not complete answers., so you’re going to have to double click on this. Architecture also determines the risk to the unauthorized viewing of data in flight and data at rest. Here are more good follow up questions:
- Who manages the keys for data in flight and data at rest? Are the keys shared between customers? If one customer is attacked and keys are accessed, can the keys be used with my tenant?
- How do you prevent unauthorized access to active directory and allowing an attacker to access my cloud desktops?
- Describe how an attacker who successfully accesses another customer’s systems cannot also enter my systems?
- Can I extend my corporate standard anti-virus, anti-malware, DLP processes into the cloud desktop service? Can I use my corporate standard MFA? Or do I need a completely separate security paradigm for your cloud desktop service?
- Can you (Vendor X), gain access to my data on my cloud desktops?
Getting clear answers to these questions enables you to fully understand the level of risk to your company’s security posture.
Workspot’s Answers to Cloud Desktop Security Questions
I can’t say it strongly enough – architecture matters for security. Workspot’s architecture design follows the Principle of Least Privilege (POLP). POLP is closely tied to Zero Trust policy where no one is trusted, either inside or outside the organization. POLP allows for people and processes to only have the bare minimum access to complete a task. That means that everyone, including the cloud desktop vendors you’re considering, needs to prove how they make your organization more secure. When you double click on Workspot, here’s are the answers to the 5 questions above:
- All customers are isolated. The keys are automatically managed by Azure key service per customer, so keys are not shared or auto rotated, and no humans are involved. Customers can bring additional keys for an added layer of security.
- Active directory is fully under your control. Workspot doesn’t have any access to it for security reasons.
- All customers are isolated. Attacks are localized to just a tenant. You don’t have to worry about your neighbor breaking down your fence.
- All Workspot customers bring their corporate standard AV, AM, DLP and MFA into Azure. There is no need to create a separate security process, which increases the risk of gaps.
- Workspot’s architecture leverages an independent security layer to prevent unauthorized access to your data.
Architecture matters for security. From the beginning, we designed our cloud desktop solution to separate the data and control planes. This was a crucial architecture decision, that among many other benefits, allows our solution to stand apart from any other when it comes to security.
Find out more about how Workspot addresses the toughest cloud desktop security questions. Today, Fortune 500 companies with the most stringent IP protection and governance requirements trust their cloud desktops to Workspot. Schedule a demo so we can discuss your requirements!